Loading.....
Machine Learning in Cybersecurity: A New Frontier in IT Security
The intersection of machine learning and cybersecurity represents an exciting and transformative frontier in the realm of IT security. As our lives become increasingly entwined with technology and the internet, the need for robust protection against cyber threats has never been more apparent. This article explores the powerful synergy between machine learning and cybersecurity, highlighting the benefits, emerging security protocols, and the promises it holds for a safer digital world.

What Is Cybersecurity
At its core, cybersecurity refers to the practice of safeguarding digital systems, networks, devices, and data from unauthorized access, damage, or theft. It encompasses a wide array of strategies, technologies, and best practices designed to protect the confidentiality, integrity, and availability of digital assets. These assets can range from personal data and financial information to critical infrastructure and government secrets.
Cybersecurity operates on several fundamental objectives, each of which contributes to creating a robust defense against digital threats:
- Confidentiality: This objective ensures that sensitive information remains confidential and is only accessible to authorized individuals or systems. Through encryption and access controls, confidentiality is maintained.
- Integrity: Integrity is about ensuring that data remains unaltered and trustworthy. Measures like digital signatures, checksums, and version control help maintain data integrity.
- Availability: Cybersecurity strives to ensure that digital systems and data are available when needed. This involves redundancy, disaster recovery planning, and protections against Distributed Denial of Service (DDoS) attacks
- Authentication: Authentication is the process of verifying the identity of users or systems. Common methods include passwords, biometrics, and two-factor authentication (2FA).
- Authorization: After authentication, authorization determines what actions or data a user or system is allowed to access. Access control lists and permissions are key elements of authorization.
- Non-Repudiation: Non-repudiation ensures that parties involved in a digital transaction cannot deny their involvement. This is established through digital signatures and comprehensive audit trails.
Benefits Of Machine Learning In Cybersecurity
Machine Learning (ML) has become a cornerstone in the field of cybersecurity, providing numerous advantages in identifying and mitigating threats. As the digital landscape evolves, so do the tactics of cybercriminals, making it essential for organizations to leverage cutting-edge technologies. In this article, we will explore the top five benefits of using ML in cybersecurity.
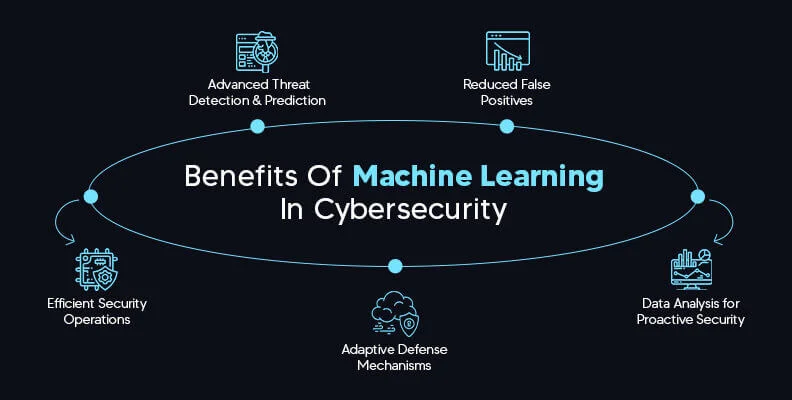
- Advanced Threat Detection and Prediction
- Reduced False Positives
- Efficient Security Operations
- Adaptive Defense Mechanisms
- Data Analysis for Proactive Security
Machine Learning algorithms excel at identifying patterns and anomalies within large datasets. In cybersecurity, this capability is invaluable. ML models can analyze massive volumes of data from network logs, user behavior, and system activity to identify unusual patterns or potential threats. By continuously learning from historical data, ML can adapt to evolving threats and effectively predict and detect new attack vectors. This proactive approach helps organizations stay one step ahead of cybercriminals, reducing the risk of breaches and data loss.
ML can automate routine cybersecurity tasks, such as log analysis, malware detection, and threat categorization. This automation streamlines security operations, enabling organizations to respond faster to emerging threats. Moreover, ML algorithms can prioritize alerts based on the severity and potential impact, ensuring that security teams address the most critical issues first. By reducing the manual workload, ML empowers cybersecurity professionals to make better use of their expertise in tackling complex, high-priority security challenges.
Traditional cybersecurity tools often generate a high volume of false positives, leading to alert fatigue for security teams. Machine Learning algorithms can significantly reduce false alarms by fine-tuning their analysis based on past incidents and known attack patterns. By learning to distinguish normal behavior from suspicious activity, ML systems enhance the accuracy of threat detection. This, in turn, allows security professionals to focus on genuine threats, improving the overall efficiency of incident response.
Cyber threats constantly evolve, necessitating adaptive defense mechanisms. Machine Learning plays a vital role in creating security systems that can adjust in real-time. ML models can analyze ongoing attacks, identify new threat vectors, and adapt their defenses accordingly. This adaptability is crucial in countering sophisticated threats, such as zero-day vulnerabilities and polymorphic malware. ML-driven security solutions can update their algorithms and strategies without human intervention, making them highly resilient against emerging threats.
ML's data analysis capabilities extend beyond threat detection. It can also be harnessed for proactive security measures. By examining historical data and user behavior, ML can identify vulnerabilities in an organization's network and recommend security improvements. It can predict potential attack vectors and advise on preventive actions. This proactive approach not only strengthens an organization's security posture but also saves valuable time and resources by preventing security incidents before they occur.
Protocols In IoT Era
The goal of ML is to develop machines that automatically learn to make decisions. The learning is done through a training phase: By instructing a computing device to analyze some “existing” (training) data via a given ML algorithm, a ML model is developed. Such a model incorporates all the knowledge learned during the training phase and implements a function to make decisions on “future” data.
Before a ML model can be deployed in an operational environment, its performance must be assessed. To this end, some “validation” data are processed by the ML model and its predictions are either analyzed by humans or compared with some known ground truth. We can hence define a ML method as “the process for developing a ML model by using ML algorithms on some training data.”
In the current era of computing devices, most of the devices that we use are connected to the Internet in a Internet of Things environment. These devices share and transmit their data through the insecure (open) communication medium, also called the Internet. Most of the time this data is sensitive in nature (i.e., healthcare data, banking data, insurance data, other finance related data, and social security numbers). The malicious entities, such as the online attackers (hackers) are always in search of that, where they play with the things (for example, they can launch attacks, like replay, man-in-the-middle, impersonation, credential guessing, session key computation, malware injection and data modification) . Therefore, from time-to-time several researchers propose different security protocols to mitigate these attacks.
The security protocols or cyber Security protocols can be divided into different categories: “authentication protocols”, “access control protocols”, “intrusion detection protocols”, “key management protocols”, and “blockchain enabled security protocols”. The summary of these protocols is given below:
-
Authentication Protocols
-
Access Control Protocols
- User access control
- Device access control
-
Intrusion Detection Protocols
-
Key Management Protocols
-
Blockchain Enabled Security Protocols
Authentication is a process of checking the genuineness (authenticity) of someone of some device. It can be performed through some credentials or factors (i.e., username, password, smartcard, biometrics), which are closely associated with the users or device. We can have user to user authentication, user to device authentication or device to authentication. On the basis of available factors, user authentication protocols can be again divided into three categories, i.e., one-factor user authentication protocol, two-factor user authentication protocol and three-factor user authentication protocol.
Access control is a process of putting restrictions on the unauthorized access of someone or some device(s). Users or devices can access the other users or devices in a secure way after the completion of all steps of a user/device access control protocol. Access control protocols can be divided into two categories:
User access control protocol can be used for the access control of the unauthorized users, whereas device access control protocol can be used for the access control of unauthorized devices. Access control can be certificate based or certificate less. Authorization is considered as a process through which an authority (i.e., a server) determines if an entity (i.e., a client) has permission to use the resource. It is usually performed in collaboration with authentication so that the server can know who the client is who’s requesting access. It determines who has permission to access a resource and who does not.
An intrusion is something or somebody with the malicious intention. This may be some malicious programming script or some Internet attacker system, which is under the control of some hacker. Usually hackers try to inject some malware in the online devices to affect their performance or to breach the security of these devices (systems).
For the detection and mitigation of intrusion, we need a specific category of protocols that come under “intrusion detection protocols”. The intrusion detection can be performed in different ways i.e., signature based intrusion detection, anomaly based intrusion detection or hybrid intrusion detection, which is combination of both signature based and anomaly based schemes. The machine learning based or deep learning based intrusion detection (i.e., malware detection) is going very famous these days.
Key management protocols are used for secure key management among the various entities, such as some devices (for example, smart Internet of Things (IoT) devices and smart vehicles) and some users (smart home user, doctor, traffic inspector). Usually, a trusted registration authority does the registration of all entities of the communication system and then stores the secret credentials (i.e., secret keys) in their memory. We need a key management process for the fresh keys generation and their storing in the devices, key establishment and key revocation purposes. The devices/users can exchange their information in a secure way after the establishment of shared secret key (i.e., a session key), which may happen through the essential steps of an authenticated key agreement protocol.
Blockchain is one of the emerging technology of the era. Blockchain maintains data in the form of certain blocks, which are chained together with some hash values. In blockchain data is maintained in the form of distributed ledger, which is named as distributed ledger technology (DLT). All the genuine parties (sometimes miner) of the network have access to the DLT. The data that we store over the blockchain safe and secured against the various possible cyber attacks. Thus, the blockchain enabled security protocols are capable of defending the various cyber attacks .
The Synergy of Cybersecurity and ML

The uniting of cyber security and machine learning can help us in various ways. For example, enhanced security to the machine learning models, improved performance of the cyber security methods, effective detection of zero day attacks with less human intervention. However, it may suffer from various issues and security challenges, which should be handled carefully. Therefore, in this particular domain, we need some review study related to the “uniting of cyber security and machine learning” i.e., issues and challenges, various attacks, different protection schemes with their comparative study and some future research directions on which other researchers should work. Hence, we tried to conduct such studies in the proposed work .
Transform your vision into powerful software solutions with our expert development team.
Conclusion
In conclusion, the fusion of machine learning and cybersecurity represents a new frontier in IT security. As the digital landscape becomes increasingly complex and threats more diverse and sophisticated, automation through machine learning has emerged as a critical tool for overwhelmed security personnel. This partnership holds immense promise for the world of cybersecurity, offering several significant benefits.
Machine learning's ability to recognize and predict specific patterns surpasses human capabilities, enabling it to effectively combat advanced threats, malicious user behavior, and other associated risks. In an era where most devices are interconnected in the Internet of Things (IoT), sensitive data is constantly transmitted through insecure communication channels, making it a prime target for malicious entities. Security protocols, such as authentication, access control, intrusion detection, key management, and blockchain-enabled security, are essential in safeguarding these devices and data.
 Back to blog
Back to blog