Loading.....
Securing Data with ORM: SQL Injection and Other Attacks in Java

Data is the lifeblood of businesses and organizations. It drives decision-making, fuels innovation, and holds immense value. However, the very thing that makes data valuable—its accessibility—also makes it vulnerable to a range of security threats. Among these threats, SQL injection is a notorious menace that can lead to data breaches, unauthorized access, and potentially catastrophic consequences. Fortunately, Object-Relational Mapping (ORM) is a robust solution that can help Java developers safeguard their data against SQL injection and other malicious attacks.
The SQL Injection Challenge
SQL injection is a code injection technique that exploits vulnerabilities in an application's software to execute malicious SQL statements. These statements can manipulate or even expose sensitive data, compromise the integrity of the database, and sometimes gain unauthorized access to the underlying system. SQL injection attacks have plagued web applications for years, and they continue to be a prevalent threat.
Traditionally, mitigating SQL injection involved meticulously sanitizing and validating user inputs, which could be a cumbersome and error-prone task. This is where ORM comes to the rescue.
ORM: An Overview
ORM, or Object-Relational Mapping, is a programming paradigm that bridges the gap between the relational databases that store data and the Java programming language used to build applications. ORM tools like Hibernate, EclipseLink, and JPA (Java Persistence API) allow Java developers to interact with databases using a high-level, object-oriented approach. Here's how ORM helps secure data in Java:
- Parameterized Queries
- Escaping and Sanitization
- Authentication and Authorization
- Input Validation
- Auditing and Logging
One of the fundamental ways ORM prevents SQL injection is by automatically generating parameterized queries. Parameterized queries separate user input from SQL code, ensuring that malicious input cannot alter the query's structure. ORM libraries handle parameterization behind the scenes, making user input safe by treating it as data rather than executable code.
For example, in Hibernate, a safe database query looks like this:
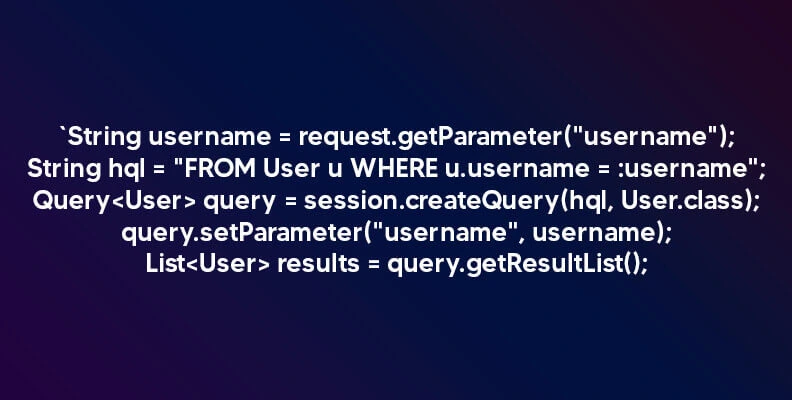
Hibernate sanitizes user input, eliminating the risk of SQL injection.
ORMs often offer built-in mechanisms for escaping and sanitizing data before it's stored in the database. This helps prevent attacks like Cross-Site Scripting (XSS) when rendering data in web applications.
For example, Hibernate can automatically escape data when rendering it in JavaServer Pages (JSP) or other view templates, reducing the risk of XSS vulnerabilities.

Securing data isn't just about preventing unauthorized access; it's also about controlling who can manipulate it. ORM libraries provide tools for defining access control rules and implementing robust authentication and authorization mechanisms.
With Java EE's security mechanisms, you can define user roles and permissions, ensuring that only authorized users can perform specific database operations.
ORMs often include features for validating user input before it's saved to the database. This helps in preventing the insertion of malicious or incorrect data.
For example, Hibernate Validator provides a wide range of built-in constraints and allows you to create custom validators to ensure data integrity.

To maintain data security, it's essential to monitor and audit database activities. ORM libraries offer hooks and event listeners that allow you to log and track changes in the database, helping identify and respond to suspicious activities or potential attacks.
Top 5 Practices for Securing Data with ORM in Java
While ORM provides robust tools for securing data, it's crucial to follow best practices to maximize security in your Java applications:
- Keep ORM and Database Software Updated: To enhance data security, it is essential to keep your ORM (Object-Relational Mapping) framework and the associated database software up to date. By doing so, you ensure that any known security vulnerabilities are promptly addressed. Regular updates and patches are crucial for maintaining a robust and secure data environment.
- Implement Strong Authentication and Authorization: Ensuring data security involves implementing robust authentication and authorization mechanisms. Utilize Java EE's security features to control access to sensitive data. Strong authentication verifies the identity of users, while authorization ensures that they have the necessary permissions to access specific data. This practice helps safeguard sensitive information from unauthorized access.
- Regular Security Configuration Reviews: Periodically reviewing and updating security configurations is a vital aspect of data protection. This includes assessing and adjusting firewall rules and database user permissions. By conducting regular security configuration reviews, you can adapt to evolving security requirements and prevent potential breaches or unauthorized access.
- Conduct Security Audits and Testing: Regularly performing security audits and penetration testing is crucial to identify and address vulnerabilities in your Java applications. These tests uncover potential weaknesses in your security measures, allowing you to take corrective actions before malicious actors exploit them. Consistent security testing is a proactive approach to data protection.
- Security Education: Educating your development teams about security best practices is fundamental. Emphasize the importance of input validation and secure coding practices specific to Java. Instructing your teams on how to handle data securely and validate inputs effectively is a preventive measure against data breaches and security risks. It empowers your developers to write code that minimizes security vulnerabilities.
Remember, security is an ongoing process, and vigilance is key to protecting sensitive data in your Java applications. By embracing ORM and adhering to best practices, you can fortify your defenses against SQL injection and other malicious attacks, ensuring your data remains safe and secure. In an era where data is king, securing it with ORM in Java is not just a choice but a necessity for every software developer and organization.
Conclusion
The significance of data in the modern business landscape cannot be overstated. It serves as the foundation for informed decision-making, innovation, and competitiveness. However, the accessibility of data also renders it susceptible to a myriad of security threats, with SQL injection being a particularly formidable adversary, capable of inflicting data breaches and unauthorized access. Thankfully, Object-Relational Mapping (ORM) emerges as a robust shield, empowering Java developers to protect their data from SQL injection and other malevolent attacks.
SQL injection, a perpetual menace to web applications, exploits vulnerabilities to execute malicious SQL statements that can compromise data integrity and security. Traditionally, safeguarding against SQL injection required meticulous input validation, a task fraught with complexity and risk. Enter ORM, a programming paradigm that offers an elegant solution.
ORM, such as Hibernate, EclipseLink, and JPA, bridges the gap between relational databases and Java applications by providing high-level, object-oriented access. It fortifies data security through various mechanisms, such as automatically generating parameterized queries, escaping and sanitization, authentication and authorization, input validation, and auditing.
In a world where data reigns supreme, securing it with ORM in Java is not merely an option; it is an imperative for every software developer and organization. Data security is an ongoing process, demanding vigilance and commitment to protect sensitive information and ensure its longevity and integrity in the digital realm. Embracing ORM and following best practices not only shields against SQL injection but also fortifies defenses against a spectrum of threats, ultimately ensuring data's safety and security.
 Back to blog
Back to blog